In the fast‑evolving world of logistics, third‑party logistics (3PL) providers are increasingly becoming hubs of digital operations—managing shipments, tracking assets, handling customer and supplier data, and interfacing with a broad network of carriers and vendors. For a brand such as 3Gistix, operating or partnering within this ecosystem means that cybersecurity isn’t simply an IT concern—it’s a business imperative.
This blog explores key cybersecurity trends affecting the 3PL space, provides relevant analytics and statistics, outlines the benefits of addressing these risks, and concludes with recommended actions.
Major Cybersecurity Trends in the 3PL Sector

Supply chain & third‑party risk escalation
Within 3PL operations, many digital and physical links extend into vendor and partner ecosystems—making them prime targets. Studies show that adding supply‑chain network features improved cyber‑risk prediction models by ~2.3 percentage points over internal‑only models.
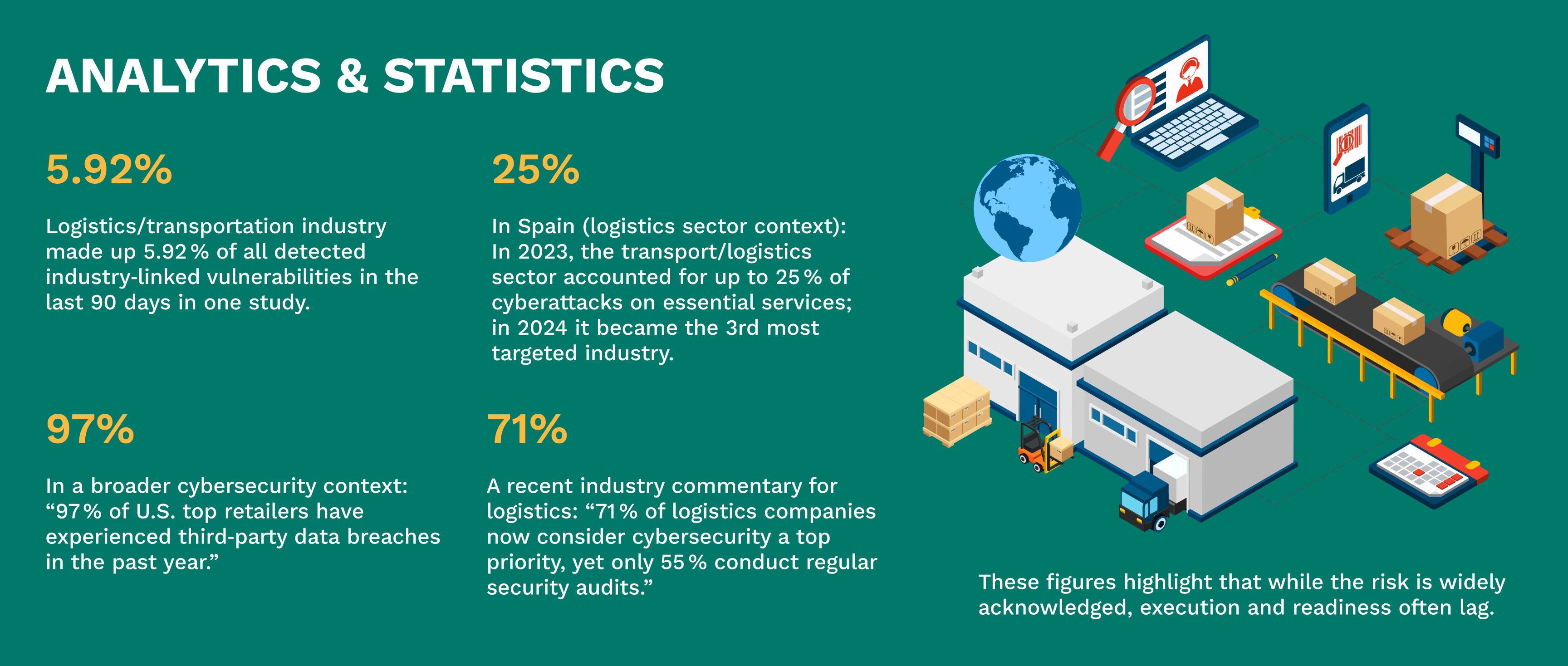
Additionally, the logistics/transportation sector recorded ~5.92 % of all detected industry‐linked vulnerabilities in a recent quarter—ranking it 5th out of 14 industries.
Why this matters for 3Gistix: As a logistics provider or user of 3PL services, your exposure isn’t only your own network—it’s the networks of your contractors, carriers, warehouses, software vendors.

Ransomware, data breaches, and operational disruption
The logistics sector is under sustained pressure from ransomware and data breach attempts. For example, recent findings indicate that logistics firms are increasingly hit by ransomware (though slightly tapering) and that data‑leak chatter is rising.
Meanwhile, industry commentary points to the dominance of ransomware and data breach activity in transport/logistics: “ransomware comprising 83.9 % of these cases and data breaches 16.1 %” in one report.
Implication for 3Gistix: A successful ransomware attack or data breach could not only incur direct costs but also cause shipment delays, reputational damage, regulatory fines, and loss of customer trust.

Increased digitisation & IoT/OT convergence
Logistics operations are becoming more connected: fleets, warehouse automation, sensors, GPS trackers, IoT devices and operational technology (OT) are now part of the network. These increase the attack surface. For example, one review noted that logistics is “especially vulnerable due to its interconnection and digital dependence.”
For 3Gistix, this means that cybersecurity isn’t just about firewalling servers—it’s about securing devices, sensors, network segments, and the full lifecycle of data flow.

Network segmentation, zero‑trust and vendor access controls becoming critical
Given the linkages to vendors, the trend is moving to active segmentation of IT and OT networks, enforcing least‑privilege vendor access, and implementing zero‑trust models. For logistics: “Apply least‑privilege access for vendor accounts… Use privileged access management (PAM) for admins and external vendors.”
Relevance to 3Gistix: If you work with multiple carriers, subcontractors, software vendors—ensuring vendor credentials, limiting lateral movement, and monitoring vendor access becomes a core security posture.

Key Benefits of Robust Cybersecurity for 3PL Providers & Clients
Reduced operational interruption
With robust prevention and response, you lower the risk of ransomware or breach‑driven stoppages (which in logistics translate to shipment delays, warehouse shutdowns, missed SLAs).
Enhanced reputation and trust
Clients and partners prefer 3PLs who can demonstrate strong cybersecurity. Being able to say “we’ve adopted vendor‑access controls, network segmentation, zero‑trust” becomes a differentiator.
Lower financial risk
Fewer incidents mean fewer costs (ransom, remediation, legal, regulatory), fewer insurance premium hikes, and less risk of contractual penalties due to downtime or breach.
Improved compliance readiness
As regulations around data protection, vendor risk and supply‑chain security tighten, having maturity in cybersecurity positions you ahead of the curve (instead of scrambling when required).
Competitive advantage in digital logistics
As logistics becomes more data‑driven (tracking, analytics, IoT), secure data handling becomes part of the value chain itself. For 3Gistix, this means you can safely monetise data or deploy new digital services with trust.
Conclusion & Recommendations
In summary: Cybersecurity trends are rapidly altering the 3PL industry’s risk profile. For 3Gistix, acknowledging these changes and embedding proactive strategies is no longer optional—it’s essential.
Recommendations for Action
- Conduct a vendor risk audit: Map out all carrier/sub‑contractor/technology vendor relationships, check their security controls, monitor access.
- Adopt network segmentation & zero trust: Separate IT (office systems) from OT/logistics systems, restrict vendor access by least‑privilege, implement strong authentication (e.g., MFA).
- Secure your IoT/OT devices and sensors: Ensure firmware updates, restrict internet exposure, monitor anomalous activity from devices in warehouse/fleet.
- Train employees and partners: Phishing, social engineering, shipment‑hijack techniques are rising—conduct drills, awareness campaigns.
- Conduct regular cybersecurity audits: Given only ~55 % of logistics firms reportedly conduct regular audits, doing so creates a strong differentiator.
- Build a response and recovery plan: Logistics operations are time‑sensitive—ensure backup and contingency plans (e.g., alternate tracking, manual workarounds) are in place.
By integrating these practices, 3Gistix can not only defend against mounting threats, but also position itself as a trusted, resilient, future‑ready logistics partner.
Resources
- ESED Cybersecurity & IT Solutions. Cybersecurity trends for the logistics sector
- VikingCloud. 207 Cybersecurity Stats and Facts for 2025
- Institute of Supply Chain Management. 3PL: Trends and Innovations Shaping the future of the Industry
- Eye Security. Top Cyber Threats in Logistics and How to Defend Against Them



